What do JBS, ColonialPipeline and Nantucket’s ferry service all have in common? Their systems were hacked and in many ways, this could have been avoided. And while these are all big-name companies, being susceptible to cyber attacks is happening more often among small to mid-sized firms.
In the asset management industry, we’re seeing an array of problems surface as a result of unpreparedness or the lack of resources to protect businesses’ sensitive information.
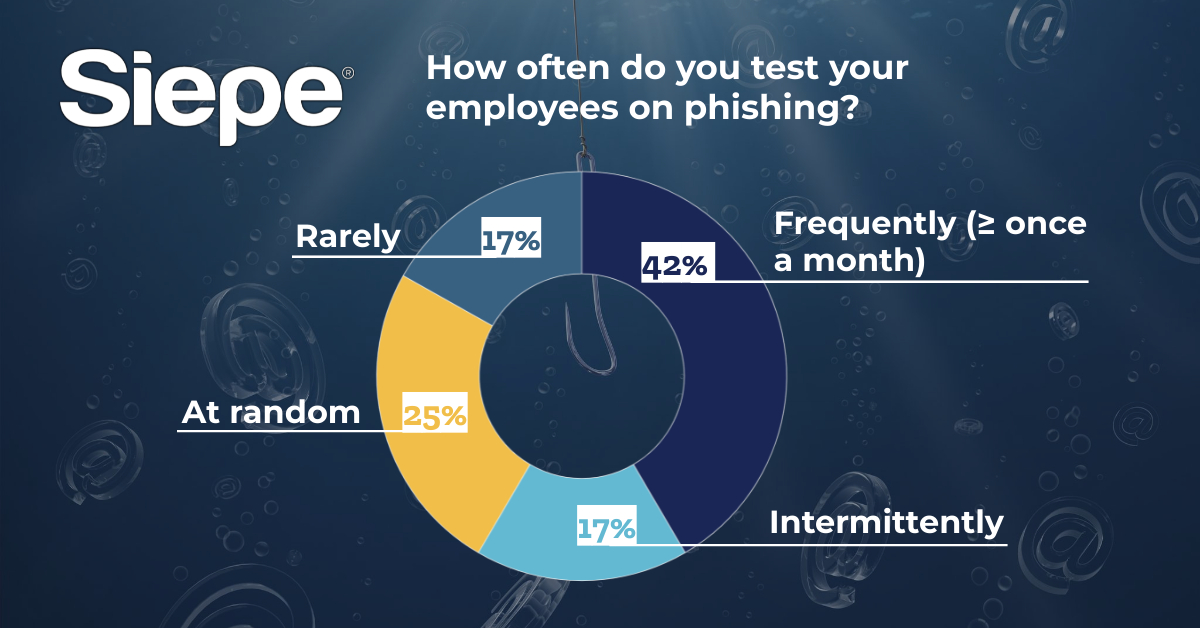
We recently conducted a survey to get an idea of how often businesses test their employees on phishing. While the results varied, we are seeing that financial firms are missing a major step in mitigating the risks of phishing attacks, particularly as firms continue operating in hybrid work environments. Frequent testing and cybersecurity protocols are necessary measures to ensure businesses are not exposed to cyber attacks or data breaches.
How often do you test your employees on phishing?
- Frequently (≥ once a month): 42%
- Intermittently: 17%
- At random: 25%
- Rarely: 17%
Understanding the relationship between cyber attacks and phishing
So how does the largest pipeline system for refined oil products in the U.S. get hacked so easily? Put simply, their systems were not protected enough from potential threats. In order to avoid cyber attacks, it’s important to understand the various forms that are out there that can lead firms of all sizes to compromise sensitive information.
Phishing is a cybercrime that involves targeting a mass group by some form of communication, such as email, telephone, text message or simply someone posing as a legitimate person or institution in order to retrieve sensitive information and data.
Spear phishing is a form of phishing that involves targeting a specific person, organization or business, and may appear more legitimate than a regular phishing attack because the details aimed at the targeted person or organization are often very personal and real. This is how employees are tricked into thinking they are accessing normal websites – it’s often difficult to tell that the person reaching out is an attacker because the email domain appears familiar.
Is the attacker a known or unknown person?
Most hacks this year came from counterparties or individuals who requested money and changed their wire details. These scenarios are much more common these days and most organizations don’t understand how to securely handle them. The issue in the investment management space is not necessarily a malicious party gaining access and holding systems hostage. Rather, an email wire is sent, the attacker patiently waits to intercept it, changes the wire instructions, and sends it to the bank on your behalf. At this point, it is very difficult – and oftentimes impossible – to retrieve the money.
What businesses need to safeguard their financial information
There are very practical steps that can be taken to avoid these scenarios altogether. Take the Colonial Pipeline hack for example, which occurred using a legacy Virtual Private Network (VPN) system that did not have multi-factor authentication (MFA) in place. That means the system was accessed through a password without a second step or layer to verify the individual’s identity, such as a text message or fingerprint.
In a recent study of businesses using Microsoft 365, 33% have not implemented Multi-Factor Authentication across all users and those who use third-party solutions reported the lowest rate of email security breaches. This is why additional password security is an extremely important factor that should not be dismissed when considering cybersecurity protocols. For example, financial firms can set up an MFA with a bank as part of the approval process for transactions or wiring money, and for all websites that require a password. Another form of password security is through a password management tool such as LastPass, 1Password, or Bitwarden. These platforms are built with a secure, behind-the-scenes protocol to authenticate users to cloud, mobile, legacy and on-premise apps.
Financial firms also need a method for controlling, detecting, and preventing unauthorized access. This can be set up through software that provides automated alerts for advanced security threats (e.g. Cisco Umbrella). In addition, web application firewalls must be in place to prevent access to suspicious websites.
And finally, as indicated by our initial survey, it’s important for firms of all sizes to test their employees often on phishing attacks. It is very easy to overlook the small details of day-to-day interactions that could be exposing your entire firm to the next cyber attack.
Contact us today to see how we can help safeguard your business from cyber attacks.